───✱*.。:。✱*.:。✧*.。✰*.:。✧*.。:。*.。✱ ───
Recently, one of my professors fell victim to malware through a malicious link. I was curious, so he sent me the link and I did a small analysis with my little knowledge in malware.
Target
This malware targets people through Discord, and it aims to sell Discord accounts, as well as to steal information such as browser passwords, browser cookies, and cryptocurrency wallets.
Malware Analysis
The website of the malware is hosted via Netlify, which has now been taken down. However, I was able to get a small snapshot of the website while it was still up.
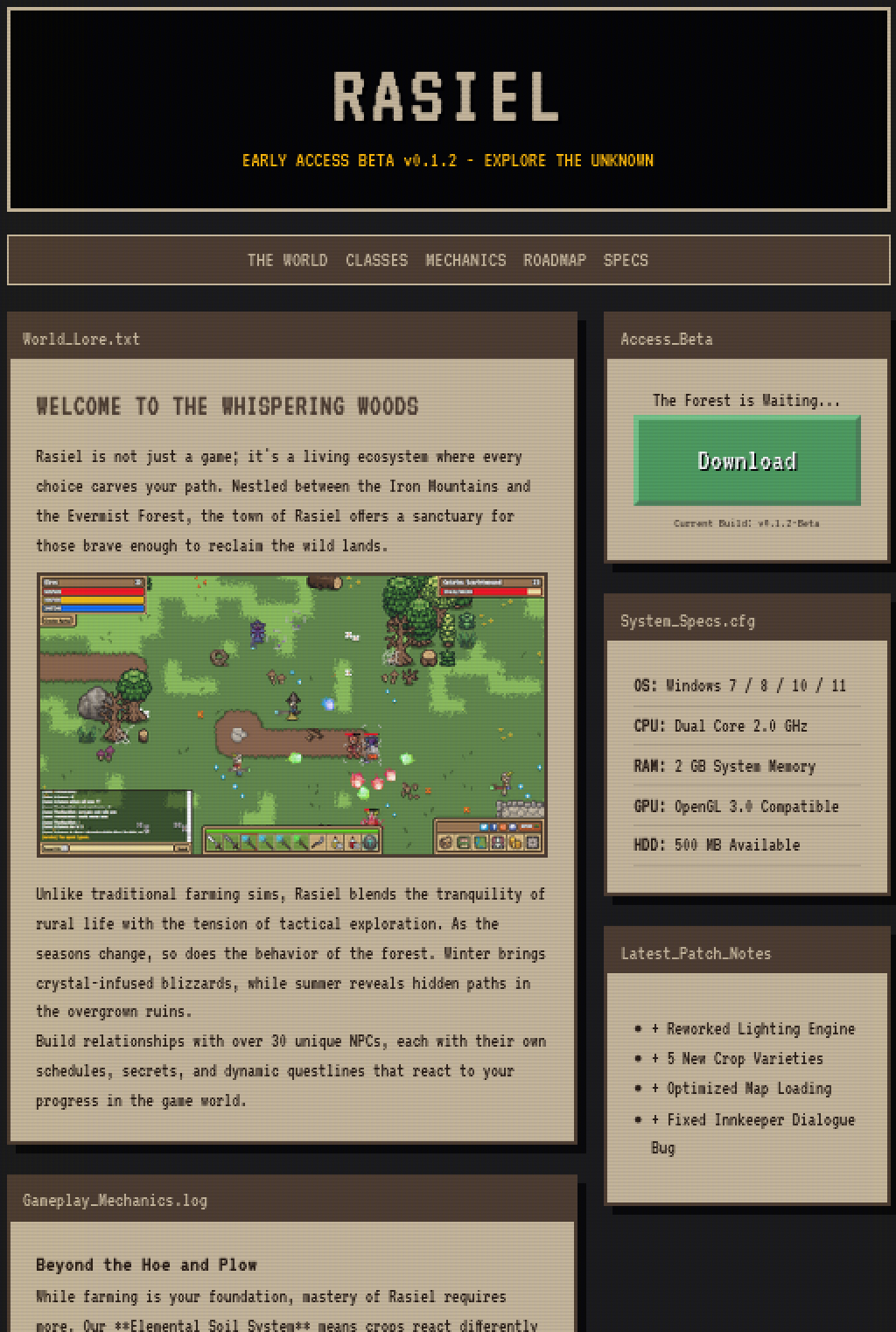
The website was relatively unsuspecting, it looks like a normal website for an indie game. However, the download button links to a malicious executable hosted within Dropbox.
Downloading the Malware
If you download the malware, it immediately starts scraping your files for browser passwords, browser cookies, and cryptocurrency wallets.
I was able to scrape together pieces of the source code of the malware, and I was able to identify that it searches the following directories for credentials:
%APPDATA%\discord\%APPDATA%\discordcanary\%APPDATA%\discordptb\%APPDATA%\discorddevelopment\%APPDATA%\lightcord\%LOCALAPPDATA%\Google\Chrome\User Data\Default\%LOCALAPPDATA%\BraveSoftware\Brave-Browser\User Data\Default\%LOCALAPPDATA%\Yandex\YandexBrowser\User Data\Default\%LOCALAPPDATA%\Microsoft\Edge\User Data\Default\%APPDATA%\Opera Software\Opera GX Stable\%APPDATA%\Opera Software\Opera Stable\%APPDATA%\Roaming\Exodus\
In the source code, it also searches for specific browser extension settings, which will store information such as secret keys for cryptocurrency wallets like MetaMask.
- MetaMask
- Exodus
- Zerion
- Phantom
- Coinbase
- Rabby
- Keplr
- Magic_Eden
- Ronin
- Trust
Nuking Their Webhook
After I deobfuscated their source code, I was able to identify that they were using a Discord webhook to send the stolen information to their server.
With this, I wrote a little Python script to send this message, every second, to their webhook:
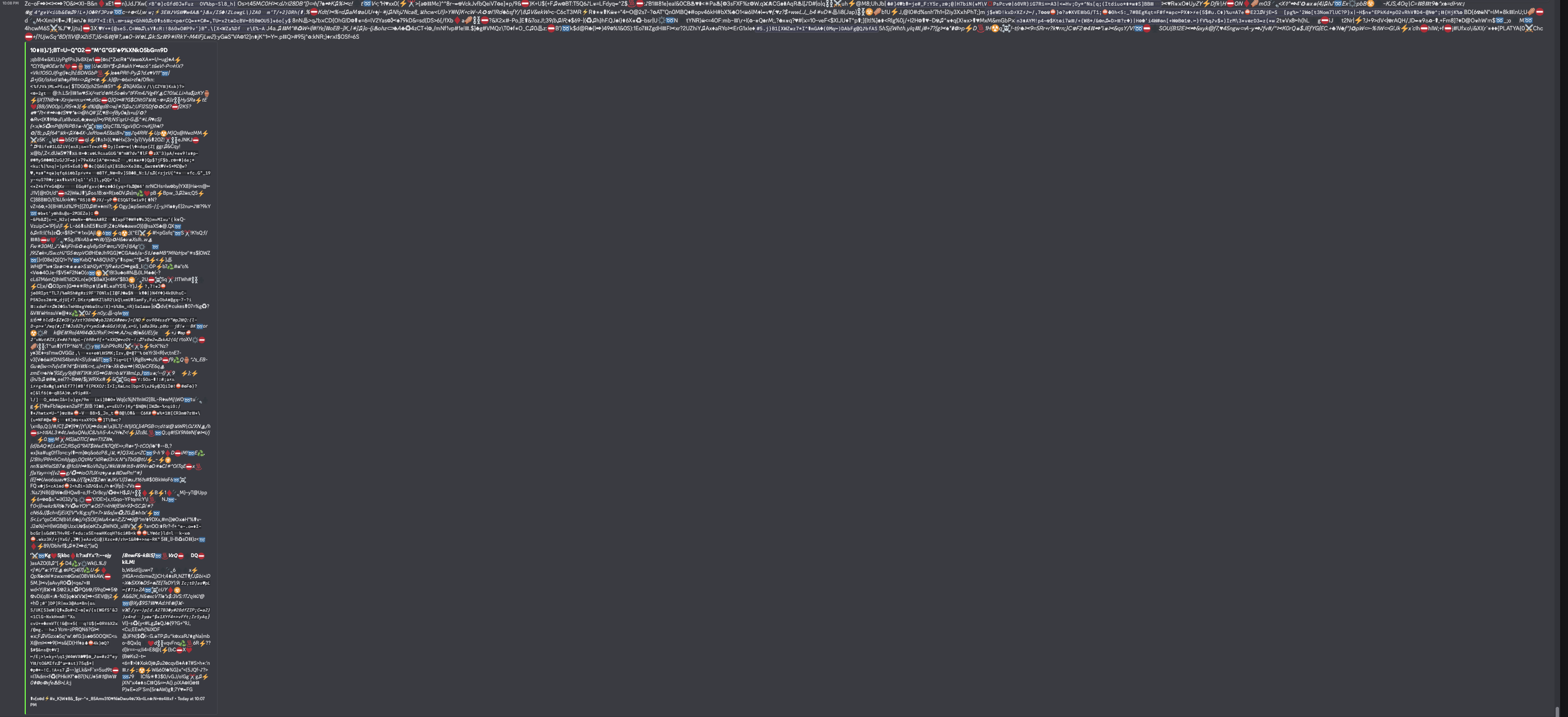
This was an attempt to get them to remove the webhook, which would effectively be a “kill switch” for the malware to send the stolen information to their Discord server.
This worked, after sending this message every second for about 2 hours, it returned a 404 error, indicating that the webhook was removed.
Unforunately, they replaced the malware with a newer .exe file, which had another webhook URL that I also nuked.
Interesting Finds
Within their source code, there were a few interesting Turkish strings that I found to be a little funny. It also had a “VM check”, but it was never actually ran, so I’m not really sure what it was for.
For instance, once it finds that you have a cryptocurrency wallet, it sends “wallet dustu omg” (“wallet found omg”) as well as “anani sikeyim wallet oha” (“I’ll f*ck your mother wallet, wow”).
It also had a check for “high quality friends”; it would check your Discord friend list for other users with things that are deemed as high quality, such as having certain badges or having an account age that was more than a few years old.
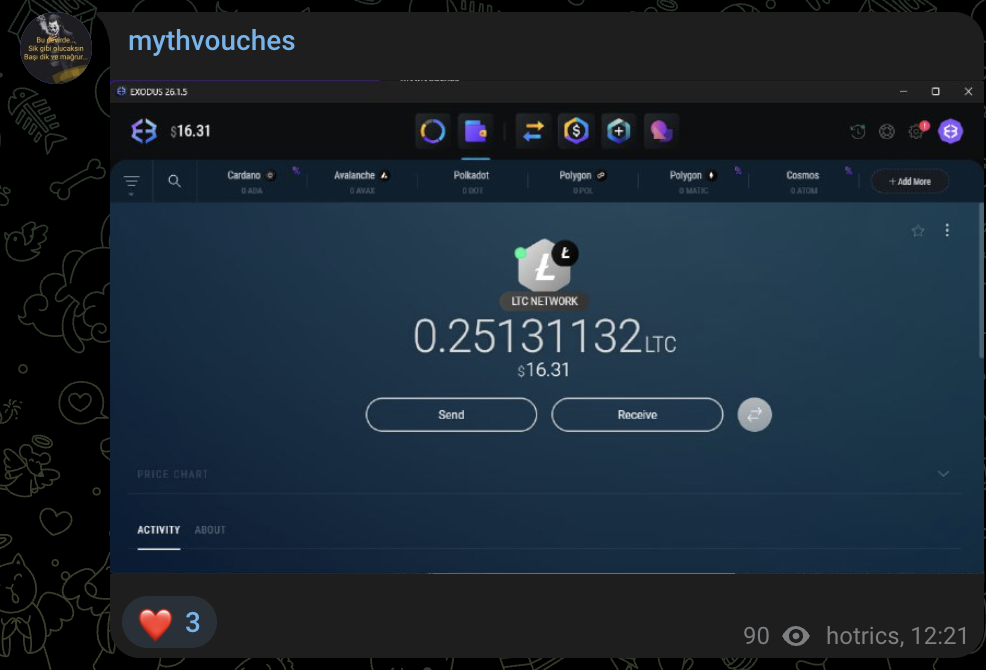
In their source code, they also advertised their Telegram channel, which I was able to join and see a few messages from them. For instance, they were bragging about their accounts that they stole, and their crypto wallets with $17 worth of LiteCoin.
Conclusion
Don’t click on random links sent from people on Discord, even if they are your friend and they want you to test your game. You should also probably run a virus scan on any file that aren’t from a trusted source.
───✱*.。:。✱*.:。✧*.。✰*.:。✧*.。:。*.。✱ ───